A Python package to cluster and visualize data from open card sorting tasks









Cardsort helps UX researchers quickly analyse data from open card sorting exercises using hierarchical cluster analysis. This task helps to understand how people organize information, and is frequently used to develop information architectures for websites. Click here to learn more about the card sorting method.
More precisely, cardsort helps you to:
- Create distance matrices using hierarchical cluster analysis
- Create dendrograms from based on these matrices
- Extract user-generated category-labels
- Using data exports from kardsort.com
Table of Contents
Documentation
cardsort.readthedocs.io
Quick start
Installation
$ pip install cardsort
Usage
cardsort can be used to create dendrograms and extract user-generated category-labels:
from cardsort import analysis
import pandas as pd
path = "example-data.csv"
df = pd.read_csv(path)
The data used in this example can be found under /docs/example-data.csv.
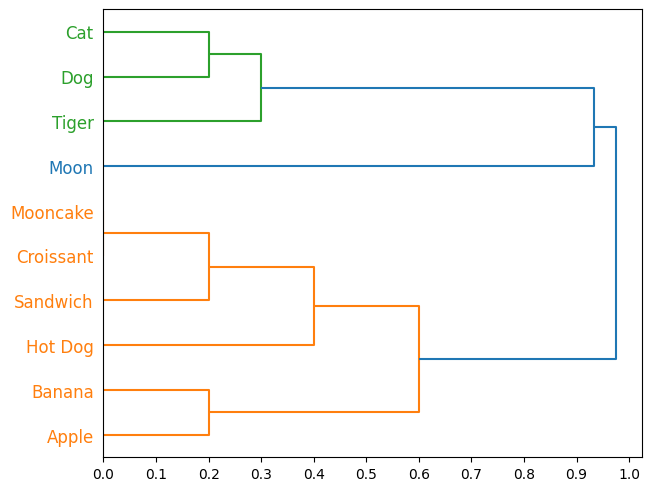
Create a dendrogram that summarizes user-generated clusters
analysis.create_dendrogram(df)
Output
Learn which category labels users gave to clusters
cards = ['Banana', 'Apple']
analysis.get_cluster_labels(df, cards)
Output
user_id cluster_label cards
0 2 Healthy snacks [Banana, Apple]
1 3 Snacks [Sandwich, Croissant, Banana, Mooncake, Apple]
2 4 Fruits [Apple, Banana]
3 5 Food [Banana, Croissant, Apple, Sandwich, Hot Dog, ...
Interpretation: In this case, the users with IDs 2 and 4 made clusters containing exactly the two cards of interest ('Banana' and 'Apple', as specified in the input variable 'cards'). User 2 labelled this cluster 'Healthy snacks', and user 4 'Fruits'. Users 3 and 5 also clustered these cards together, but they included additional other cards in the same cluster, and labelled the cluster 'Snacks' or 'Food'. User 1 does not appear in the output, because they did not cluster the cards together.
Accepted data
- This package works with data exports from kardsort.com (Export format 'Casolysis Data (.csv) - Recommended') or other data following the same structure.
- Columns:
card_id, card_label, category_id, category_label, user_id
Advanced usage
See documentation
Project information
License
cardsort is licensed under the of the MIT license.
Contributing
Interested in contributing? Check out the contributing guidelines. Please note that this project is released with a Code of Conduct. By contributing to this project, you agree to abide by its terms.
Citation
If you want to cite cardsort, please use the following DOI: 
Credits
cardsort was created with cookiecutter and the py-pkgs-cookiecutter template.
Contributors
Thanks goes to these wonderful people (emoji key):
This project follows the all-contributors specification. Contributions of any kind welcome!











