Linktools Toolkit
开始使用
依赖项
python & pip (3.6及以上): https://www.python.org/downloads/
安装
使用pip安装linktools
python3 -m pip install -U "linktools[all]"
额外的依赖项以及相应功能可通过requirements.yml查看
配置alias(推荐)
对于*nix等系统,推荐在~/.bashrc 或 ~/.bash_profile 或 ~/.zshrc等文件中配置,简化调用方式,如:
eval "$(python3 -m linktools.cli.env alias --shell bash)"
eval "$(ct-env --silent java 17.0.11 --shell bash)"
alias adb="at-adb"
alias sib="it-sib"
alias pidcat="at-pidcat"
alias apktool="ct-tools apktool"
alias burpsuite="ct-tools burpsuite"
alias jadx="ct-tools --set version=1.5.0 jadx-gui"
相关功能
$ python3 -m linktools
___ __ __ __
/ (_)___ / /__/ /_____ ____ / /____
/ / / __ \/ //_/ __/ __ \/ __ \/ / ___/ linktools toolkit (v0.8.14)
/ / / / / / ,< / /_/ /_/ / /_/ / (__ ) by: Hu Ji <669898595@qq.com>
/_/_/_/ /_/_/|_|\__/\____/\____/_/____/
📎 All commands
├── 📖 at: Android scripts
│ ├── 👉 adb: Manage multiple Android devices effortlessly with adb commands
│ ├── 👉 agent: Debug and interact with android-tools.apk for troubleshooting
│ ├── 👉 app: Retrieve detailed information about installed applications on Android devices
│ ├── 📘 cert: Display detailed X.509 certificate information for secure communication
│ ├── 👉 debug: Debug Android apps effectively using the Java Debugger (jdb)
│ ├── 👉 frida: Use Frida for dynamic analysis on rooted Android devices
│ ├── 👉 info: Collect detailed device information
│ ├── 📘 intent: Execute common Android intent actions for automation and testing
│ ├── 👉 objection: Simplify security testing with Objection on rooted Android devices
│ ├── 👉 pidcat: Filter logcat by package name
│ └── 👉 top: Fetch basic information about the currently running application
├── 📖 ct: Common scripts
│ ├── 📘 env: Manage and configure the Linktools environment
│ ├── 👉 grep: Search and match files using regular expressions
│ └── 👉 tools: Execute tools directly from remote URLs
├── 📖 it: iOS scripts
│ ├── 👉 frida: Use Frida for dynamic analysis on jailbroken iOS devices
│ ├── 👉 ios: Manage multiple iOS devices effortlessly with go-ios commands
│ ├── 👉 ipa: Parse and extract detailed information from IPA files
│ ├── 👉 objection: Simplify security testing with Objection on jailbroken devices
│ ├── 👉 scp: Securely copy files to/from a jailbroken iOS device using OpenSSH
│ └── 👉 ssh: Remotely login to jailbroken iOS devices using the OpenSSH client
通用功能(脚本前缀为ct-)
👉 ct-env
环境配置相关命令
常用命令
$ ct-env --silent alias --shell bash
$ ct-env --silent java 17.0.11 --shell bash
$ ct-env shell
$ ct-env clean 7
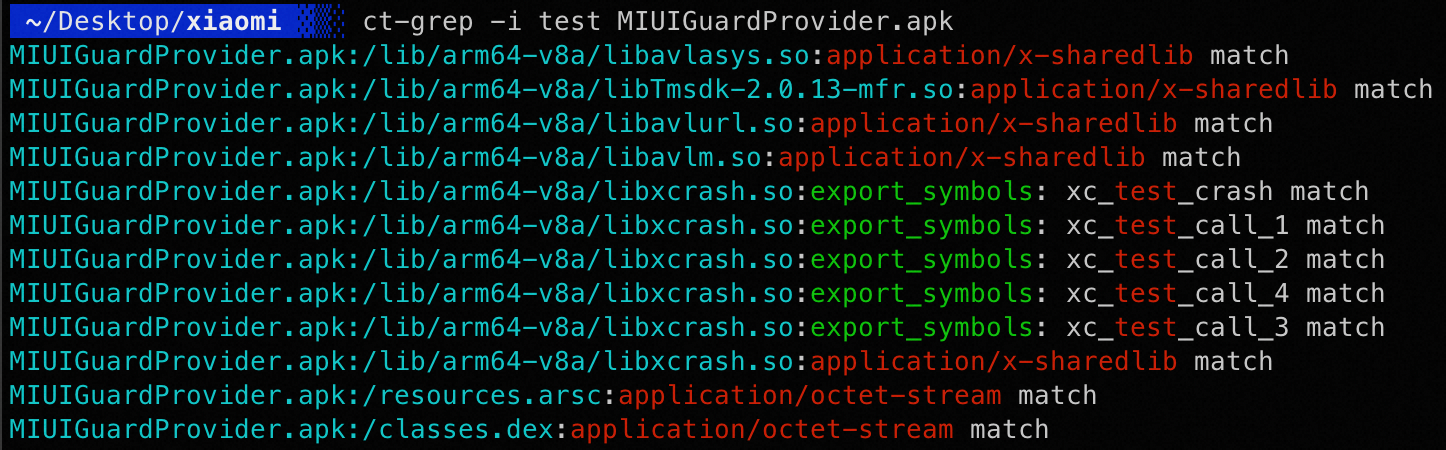
👉 ct-grep
类似linux中的grep,正则匹配文件内容 ,额外添加解析zip、elf等格等功能
👉 ct-tools
读取配置文件,即可下载使用对应工具,声明了adb、jadx、apktool、baksmali等常用工具
常用命令
所有声明的工具可通过配置文件查看,此处以apktool举例
$ ct-tools apktool -h
$ ct-tools --config apktool
$ ct-tools --download apktool
$ ct-tools --clear apktool
$ ct-tools --daemon apktool
$ ct-tools --set version=2.5.0 apktool
android相关功能(脚本前缀为at-)
👉 at-adb
若环境变量中存在adb可执行程序,则直接执行;否则自动下载最新版本执行。该功能支持操作多台手机
常用命令
at-adb的命令与adb命令一致,以下以adb shell举例
$ at-adb -s xxx shell
$ at-adb -l shell
$ at-adb -c 127.0.0.1:5555 shell
$ at-adb shell
More than one device/emulator
>> 1: 18201FDF6003BE (Pixel 6)
2: 10.10.10.58:5555 (Pixel 6)
Choose device [1~2] (1): 1
👉 at-pidcat
集成了pidcat,并且修复了中文字符宽度问题,原项目链接:https://github.com/JakeWharton/pidcat
常用命令
$ at-pidcat -p me.ele
$ at-pidcat --top
$ at-pidcat -t XcdnEngine
👉 at-top
显示顶层应用信息、获取顶层应用apk、截屏等
常用命令
$ at-top
$ at-top --apk
$ at-top --screen
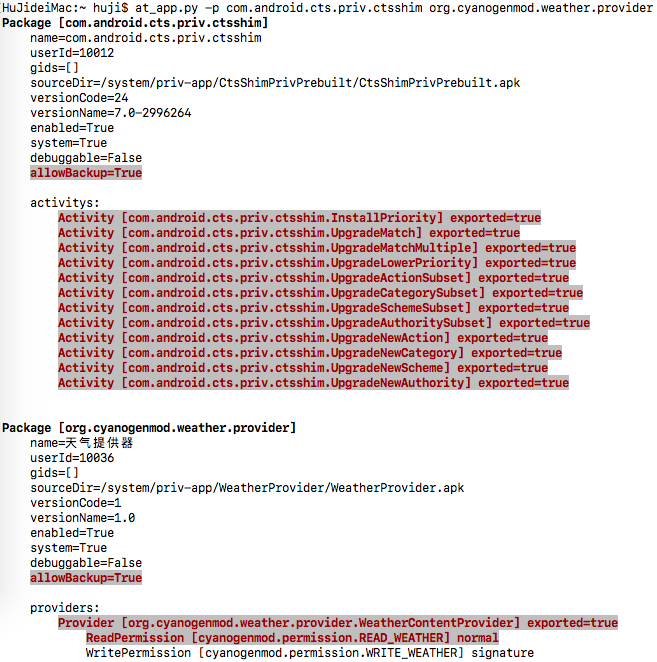
👉 at-app
通过执行agent调用pms读取app基本信息并展示,组件、权限等信息相对静态检测更为准确
常用命令
$ at-app
$ at-app --detail
$ at-app --detail --dangerous
$ at-app --non-system
输出效果
👉 at-inetnt
打包了常用intent操作,支持如打开设置界面、开发者选项界面、app设置界面、安装证书、打开浏览器链接等功能
常用命令
$ at-intent setting
$ at-intent setting-dev
$ at-intent setting-app
$ at-intent setting-cert ~/test.crt
$ at-intent install https://example.com/test.apk
$ at-intent browser https://example.com
👉 at-frida
该功能旨在方便使用frida,可自动下载server,支持加载远程脚本,并内置了常用功能
相关特性
- 可以支持根据android设备和python的frida版本,全自动完成下载、推送、运行frida server
- 监听了spawn进程变化情况,可以同时hook主进程和各个子进程
- 监听js文件变化,实时加载
- 注入了内置脚本,封装常用功能,如:过ssl pinning
- 支持加载远程脚本
- 支持重定向设备流量到本地端口
使用方式
1) 以命令行方式运行
$ at-frida -l ~/test/frida.js -p me.ele --spawn
$ at-frida -c https://raw.githubusercontent.com/linktools-toolkit/linktools/master/agents/frida/test/android.js -p me.ele --redirect-port 8080
$ at-frida --serve --remote-port 27042 --local-port 27042 -p fake_package
$ at-frida --no-serve --remote-port 27042 -p me.ele
2) 使用python方式调用
执行如下python脚本即可自动开启frida-server,并将js代码注入到指定进程,参考src/linktools/cli/commands/android/frida.py
from linktools.cli import BaseCommand
from linktools.frida import FridaApplication, FridaEvalCode, FridaAndroidServer
class Command(BaseCommand):
def init_arguments(self, parser):
pass
def run(self, args):
code = """
Java.perform(function () {
JavaHelper.hookMethods(
"java.util.HashMap",
"put",
{stack: false, args: true}
);
});
"""
with FridaAndroidServer() as server:
app = FridaApplication(
server,
user_scripts=(FridaEvalCode(code),),
enable_spawn_gating=True,
target_identifiers=rf"^com.topjohnwu.magisk($|:)"
)
app.inject_all()
app.run()
command = Command()
if __name__ == "__main__":
command.main()
内置接口
e.g. java相关接口
Java.perform(function () {
JavaHelper.hookMethod(
"me.ele.privacycheck.f",
"a",
['android.app.Application', 'boolean'],
function (obj, args) {
args[1] = true;
return this(obj, args);
}
);
JavaHelper.hookMethods(
"anet.channel.entity.ConnType",
"isHttpType",
() => true
);
JavaHelper.hookAllMethods(
"p.r.o.x.y.PrivacyApi",
JavaHelper.getEventImpl({
stack: true,
args: true,
thread: false,
extras: {
customKey1: "自定义参数",
}
})
);
JavaHelper.use("p.r.o.x.y.PrivacyApi", function(clazz) {
JavaHelper.hookAllMethods(
clazz,
JavaHelper.getEventImpl({
stack: true,
args: true,
})
);
});
JavaHelper.bypassSslPinning();
JavaHelper.setWebviewDebuggingEnabled();
});
👉 at-agent
测试android-tools.apk时使用
常用命令
$ at-agent common --set-clipboard "剪切板内容"
$ at-agent common --get-clipboard
$ at-agent -u root --debug service --detail
$ at-agent --plugin app-release.apk
ios相关功能(脚本前缀为it-)
👉 it-ios
若环境变量中存在ios可执行程序,则直接执行;否则自动下载指定版本执行。该功能支持操作多台手机
$ it-ios list
$ it-ios -s xxx info
$ it-ios -l info
$ it-ios info
More than one device/emulator
>> 1: 00008030-001174D10CC1802E (iPhone)
2: 00008030-001174D10CC1803E (iPhone)
Choose device [1~2] (1): 1
👉 it-ssh
通过ssh连接设备,需要设备已越狱并且已安装OpenSSH
$ it-ssh
$ it-ssh sh -c "id"
👉 it-frida
该功能旨在方便使用frida,支持加载远程脚本,内置了部分常用功能,需要设备已越狱并且已安装frida
$ it-frida -h ░▒▓ ✔ 12:37:52
usage: it-frida [-h] [--version] [--verbose] [--debug] [--time | --no-time] [--level | --no-level] [-u UDID | --connect IP:PORT | --last] [-b BUNDLE_ID] [--spawn]
[-P KEY VALUE] [-l SCRIPT] [-e CODE] [-c URL] [-a]
Easy to use frida (require iOS device jailbreak)
___ __ __ __
/ (_)___ / /__/ /_____ ____ / /____
/ / / __ \/ //_/ __/ __ \/ __ \/ / ___/ linktools toolkit (v0.0.1.dev0)
/ / / / / / ,< / /_/ /_/ / /_/ / (__ ) by: Hu Ji <669898595@qq.com>
/_/_/_/ /_/_/|_|\__/\____/\____/_/____/
options:
-h, --help show this help message and exit
--version show program's version number and exit
-b BUNDLE_ID, --bundle-id BUNDLE_ID
target bundle id (default: frontmost application)
--spawn inject after spawn (default: false)
-P KEY VALUE, --parameters KEY VALUE
user script parameters
-l SCRIPT, --load SCRIPT
load user script
-e CODE, --eval CODE evaluate code
-c URL, --codeshare URL
load share script url
-a, --auto-start automatically start when all processes exits
log arguments:
--verbose increase log verbosity
--debug enable debug mode and increase log verbosity
--time, --no-time show log time
--level, --no-level show log level
sib arguments:
-u UDID, --udid UDID specify unique device identifier
--connect IP:PORT use device with TCP/IP
--last use last device





