
Security News
vlt Launches "reproduce": A New Tool Challenging the Limits of Package Provenance
vlt's new "reproduce" tool verifies npm packages against their source code, outperforming traditional provenance adoption in the JavaScript ecosystem.
SRP Module for Alliance Auth
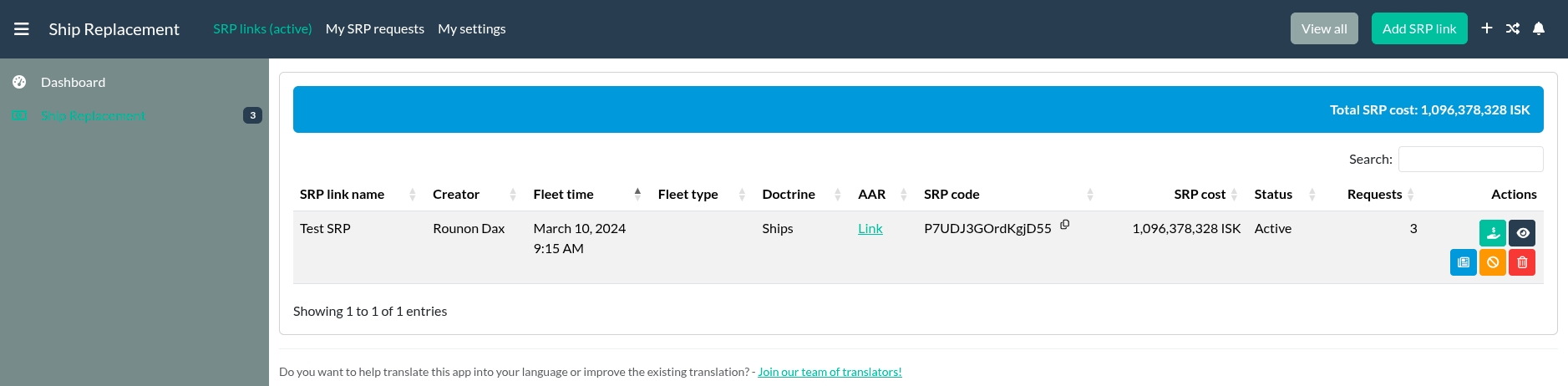
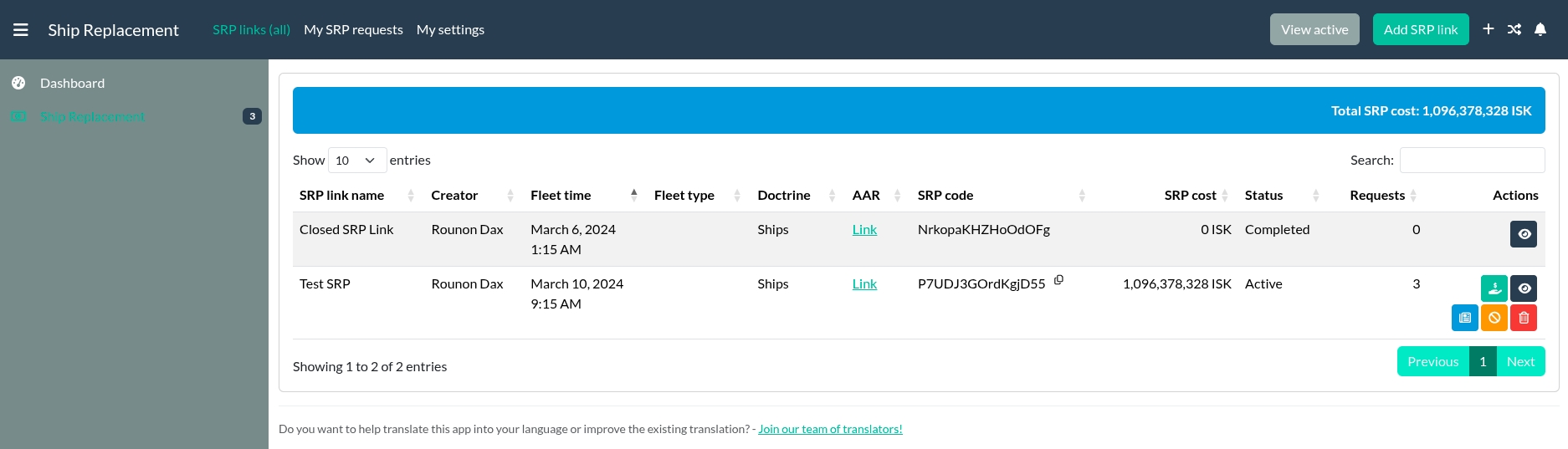
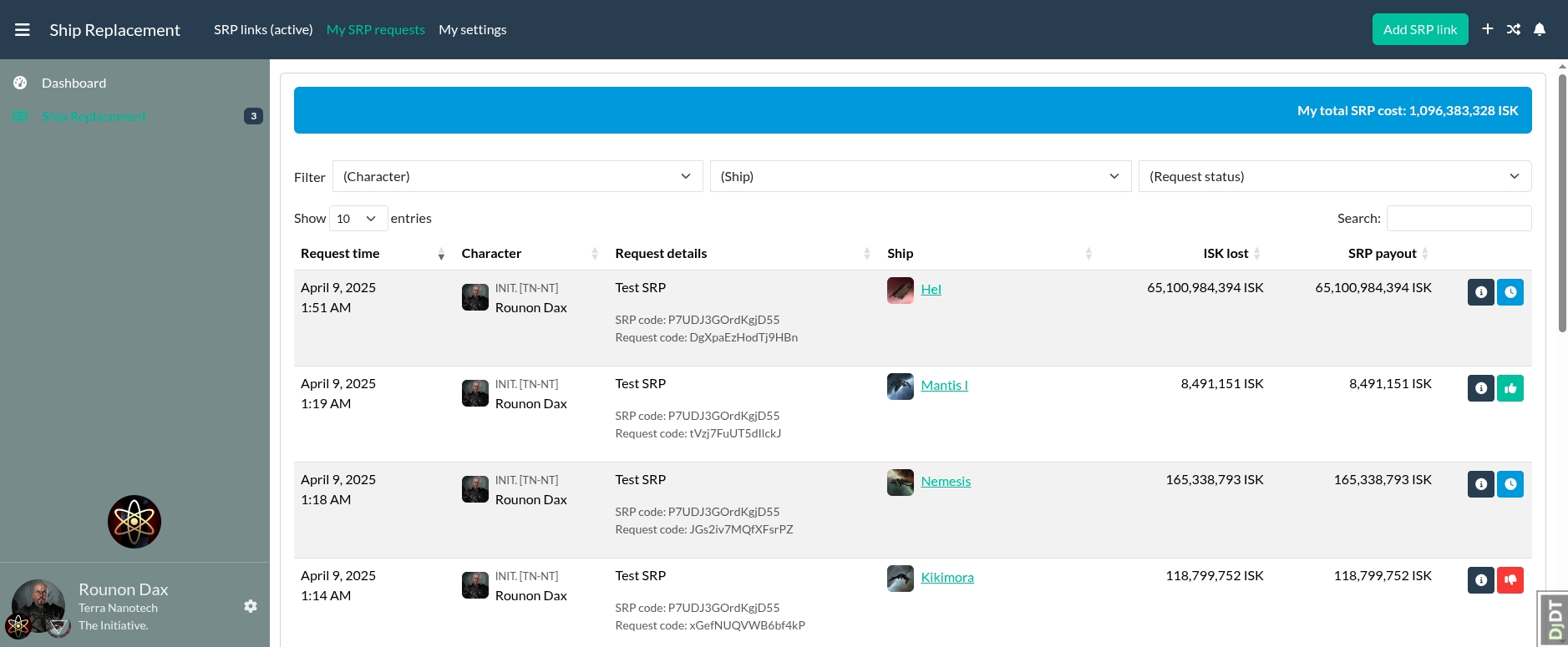
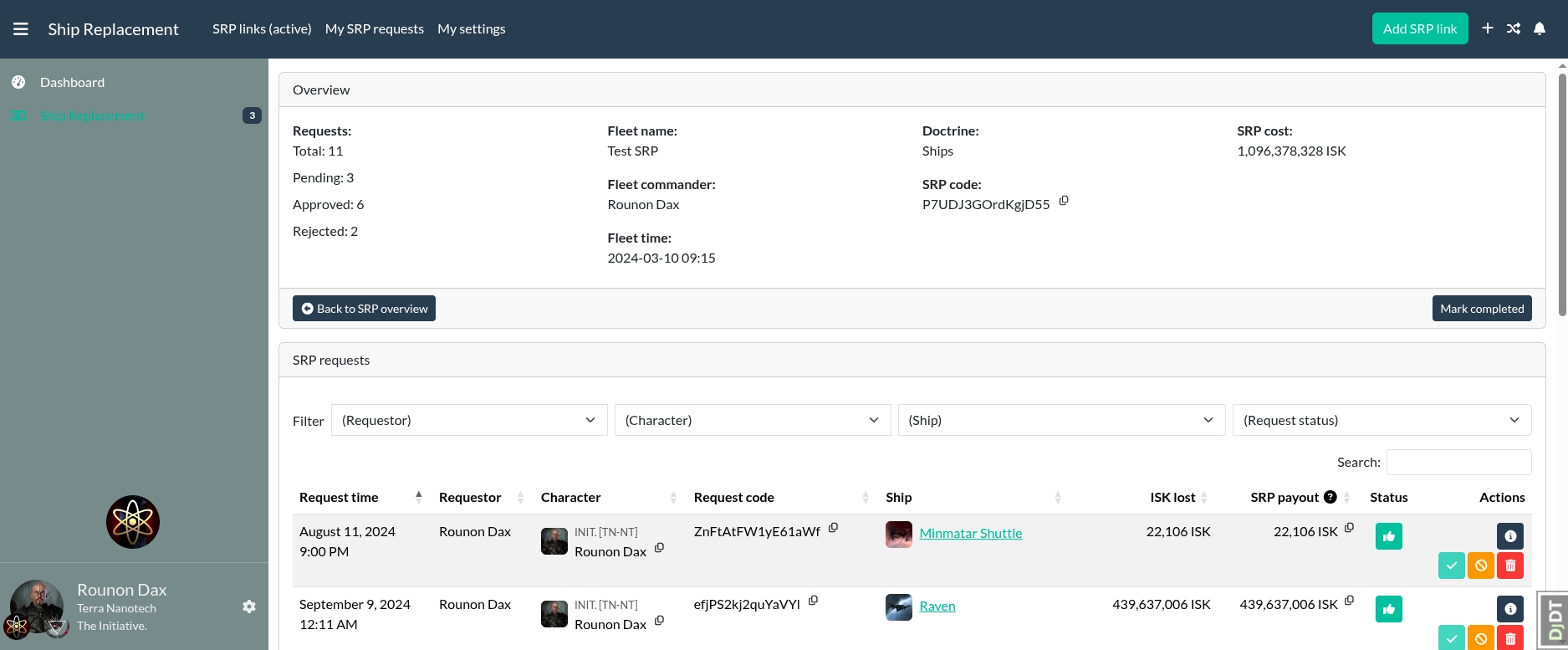
[!NOTE]
AA SRP >= 2.0.0 needs at least Alliance Auth v4.0.0!
Please make sure to update your Alliance Auth instance before you install this module or update to the latest version, otherwise an update to Alliance Auth will be pulled in unsupervised.
The last version of AA SRP that supports Alliance Auth v3 is
1.21.0.
Important: Please make sure you meet all preconditions before you proceed:
Make sure you're in the virtual environment (venv) of your Alliance Auth installation Then install the latest release directly from PyPi.
pip install aa-srp
This is fairly simple, just add the following to the INSTALLED_APPS of your local.py
Configure your AA settings (local.py) as follows:
"eveuniverse", to INSTALLED_APPS"aasrp", to INSTALLED_APPSRun static files collection and migrations
python manage.py collectstatic
python manage.py migrate
Restart your supervisor services for Auth
AA SRP utilizes the EveUniverse module, so it doesn't need to ask ESI for ship information. To set this up, you now need to run the following command.
python manage.py aasrp_load_eve
Now it's time to set up access permissions for your new SRP module. You can do so in your admin backend in the AA SRP section. Read the Permissions section for more information about the available permissions.
This step is only needed when you have been using the built-in SRP module until now.
Make sure you don't have any open SRP requests before. All SRP links in the built-in module will be closed during the import process, to make sure to not import any duplicates.
The import process can be done at any given time and doesn't necessarily have to be during the installation.
To import your SRP information from the built-in SRP module, run the following command.
python manage.py aasrp_migrate_srp_data
If you are using Discord Proxy to send Discord messages, you can configure the host and port in your local.py settings.
| Name | Description | Default |
|---|---|---|
DISCORDPROXY_HOST | Hostname used to communicate with Discord Proxy. | localhost |
DISCORDPROXY_PORT | Port used to communicate with Discord Proxy. | 50051 |
| ID | Description | Notes |
|---|---|---|
basic_access | Can access the AA SRP module | Your line members should have this permission. |
create_srp | Can create new SRP links | Your FCs should have this permission. |
manage_srp | Can manage SRP | Users with this permission can manage the AA SRP Module. Like changing and removing SRP links and requests. |
manage_srp_requests | Can manage SRP requests | Users with this permission can manage the SRP requests. Like changing and removing SRP requests. |
See CHANGELOG.md
Do you want to help translate this app into your language or improve the existing translation? - Join our team of translators!
You want to contribute to this project? That's cool!
Please make sure to read the Contribution Guidelines.
(I promise, it's not much, just some basics)
FAQs
Improved SRP Module for Alliance Auth
We found that aa-srp demonstrated a healthy version release cadence and project activity because the last version was released less than a year ago. It has 1 open source maintainer collaborating on the project.
Did you know?

Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Security News
vlt's new "reproduce" tool verifies npm packages against their source code, outperforming traditional provenance adoption in the JavaScript ecosystem.

Research
Security News
Socket researchers uncovered a malicious PyPI package exploiting Deezer’s API to enable coordinated music piracy through API abuse and C2 server control.

Research
The Socket Research Team discovered a malicious npm package, '@ton-wallet/create', stealing cryptocurrency wallet keys from developers and users in the TON ecosystem.